Content management error: Header Banners should not be placed in the Navigation placeholder!
Serverless Managed Identity and Authorisation for SLA Reporting
David Banks Posted 27 August 2021Content management error: Generic Content Banners should not be placed in the Navigation placeholder!
The Scenario
A state government agency operates a portal to display SLA reporting to its industry partners.
The public-facing portal required a robust security solution providing authentication and authorisation. The users of this system come from both external parties and the customers’ own staff.
A key focus of the solution was to leverage fully managed services as much as possible for the storage and operation of an identity store, so that it can be proactively maintained and protected from abuse.
Advanced features like Multi-Factor authentication, credential reset workflows, and more, were required to ensure the solution for identity was as self-service as possible for the end user, and not adding additional administrative burden to the application management team.
Modis architected, implemented and manages the solution for our customer as a Managed Services Provider. The solution was implemented in early 2021.
Content management error: Generic Content Banners should not be placed in the Navigation placeholder!
The Solution
Modis leveraged Amazon Cognito, providing both a local user pool for external parties and SAML federation back to Active Directory Federation server to our customer’s Active Directory Domain.
With the application deployed into a modern web server, it established a trust relationship to the Cognito Identity Provider, thus resting the responsibility for all authentication into one fully-managed solution.
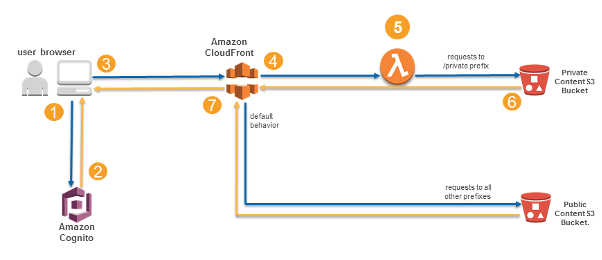
Figure 1 Trust relationships for the Portal application
Here is how the solution works:
- The viewer’s web browser is redirected to Amazon Cognito custom UI page to sign up and authenticate.
- After authentication, Cognito generates and cryptographically signs a JWT then responds with a redirect containing the JWT embedded in the URL.
- The viewer’s web browser extracts JWT from the URL and makes a request to private content (private/* path), adding Authorization request header with JWT.
- Amazon CloudFront routes the request to the nearest AWS edge location. The CloudFront distribution’s private behaviour is configured to launch a Lambda@Edge function on ViewerRequest event.
- Lambda@Edge decodes the JWT and checks if the user belongs to the correct Cognito User Pool. It also verifies the cryptographic signature using the public RSA key for Cognito User Pool. Crypto verification ensures that JWT was created by the trusted party.
- After passing all of the verification steps, Lambda@Edge strips out the Authorization header and allows the request to pass through to designated origin for CloudFront. In this case, the origin is the private content Amazon S3 bucket.
- After receiving response from the origin S3 bucket, a JSON. CloudFront sends the response back to the browser. The browser displays the data from the returned JSON file. The JSON file is then read and then looped through retrieving Image files listed within the JSON. As the Image cannot be directly accessed the files are converted to dynamic images that are then displayed. These new images are only valid for this browser session.
Content management error: Generic Content Banners should not be placed in the Navigation placeholder!
The Outcome
As the configured solution leveraged fully managed services, the responsibility and effort to perform critical security patching to these components is done for our customer without them needing to take any action themselves.
Furthermore, the scalability of the solution matches the usage pattern. As a Serverless pattern, the cost is also minimal. There are no operating systems to license, patch or upgrade over time, further reducing the TCO of the solution.
This then frees up the Modis manage services teams to concentrate on the business logic, metrics and observability of the system.
About Modis
At Modis we connect people, technology and businesses to the opportunities they need to thrive in a rapidly advancing world. With 1,300+ technology professionals across six locations (Sydney, Melbourne, Brisbane, Adelaide, Canberra and Perth), we work with our clients to deliver solutions and talent to transform technology portfolios, streamline business functions, drive innovation or enhance organisational capability. https://aws.modis.com
Content management error: Generic Content Banners should not be placed in the Navigation placeholder!
Content management error: Generic Content Banners should not be placed in the Navigation placeholder!

The Western Australian Government land information authority, Landgate, needed to implement a low-cost scalable solution for property reporting to pro...
In late 2019, a multi-national enterprise asked Modis to review its AWS Cloud operations. Having started their AWS Cloud journey in early 2018 and app...
Landgate needed to migrate to the cloud its Topo application used by Landgate Topographic and Geospatial teams for maintenance and dissemination of We...
Organisations are looking to detach themselves of their costly on-premise data centres, not just moving applications, but all aspects of software life...
Content management error: Generic Content Banners should not be placed in the Navigation placeholder!
Start a Conversation
Find out how Modis can provide you with innovative AWS cloud based solutions and servicesModis has been an AWS Advanced Tier Partner since 2014. Modis' AWS Cloud Consulting services encompasses fundamentals of cyber security, fault tolerant digital system architecture, modernisation, traditional virtual machine or through to modern Serverless approaches, commercial off-the-shelf software operation to bespoke software development, delivered with high throughput, repeatable DevOps approaches to operations. With over half a decade of running critical authoritative government data sets that affects the lives of millions of citizens and the economies of the state, Modis has one of the most mature, experienced and recognised consulting service providers in the world. More importantly, we like to work very closely with our customers, not providing something to purchase, but taking a deep understanding of their business, and providing the recommendations and implementations to ensure a modern, efficient, reliable and secure environment for digital business systems.Contact usWe are global leaders